This post is part of a series. Practical email security guide » Attachments and spotting malware

The days of sending and receiving viruses—literal virus files designed to spread across your computer—aren’t dead, but for most people it’s unlikely. Most built-in systems are very good at detecting threats. But it is still possible.
Here are two file attachments. Which one seems okay to you?
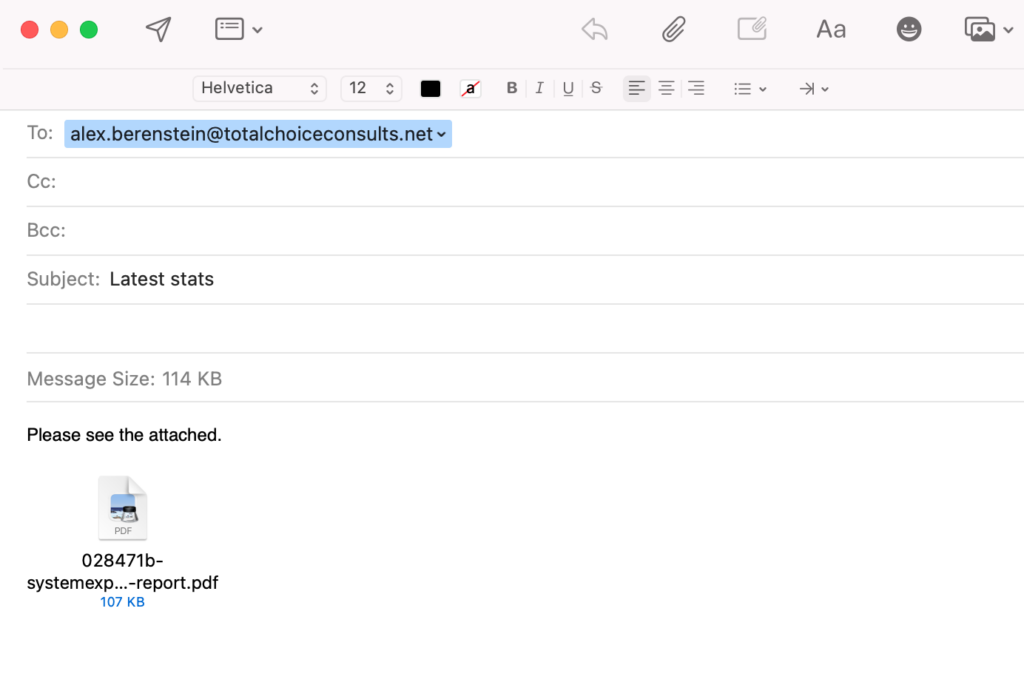
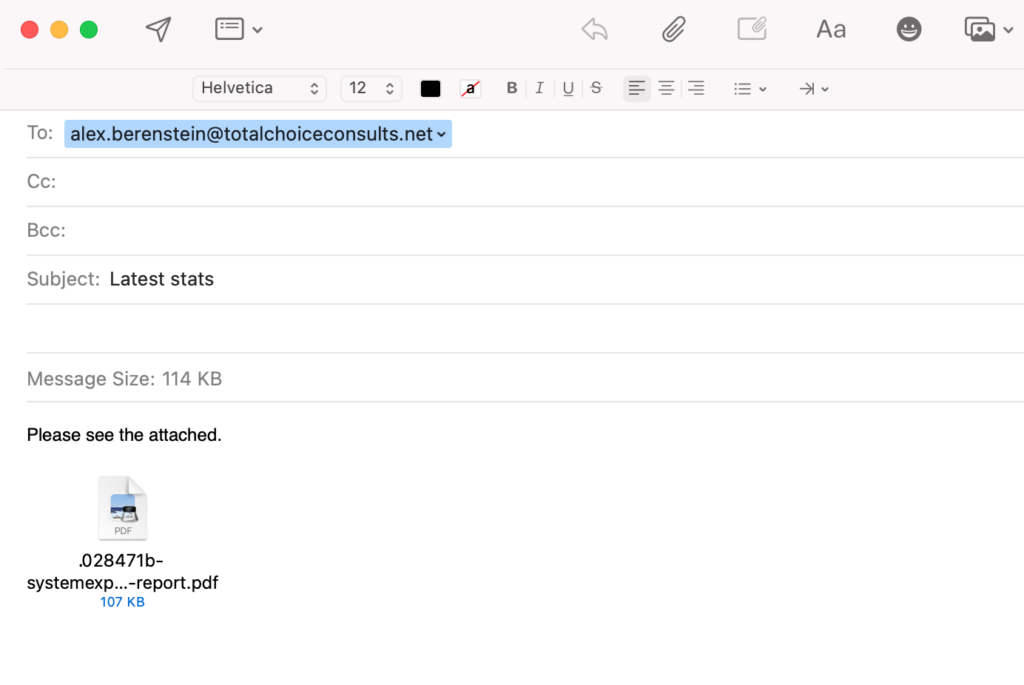
The one on the right has a period (.) in front of the file name. Across operating systems, periods are a reserved or special file character. They connote “and here’s the file extension” to the system, like a period in a sentence connotes “the end of the sentence”.
It’s small, but easy to spot when you know that. Especially with filenames that are often server-generated, long, and meaningless—such as financial record exports and files downloaded from a website.
If in doubt, just leave it alone.
Tip: your phone is more secure from malicious attachments
Tip: if in doubt about opening a file extension, even from someone you think is trustworthy, reach for your phone instead. Most phones are incapable of rendering malicious files the same way laptops and PCs can.
This isn’t great advice, but if you’re only sort of unsure, your phone is more likely to render the attachment with a vague “unable to open file” error and do nothing else. .exe files, .dll, .dmg, and .rar files are good examples of file extensions phones just won’t do anything with because no app is in the system to execute them. .zip files however, can be opened anywhere and contain any number of things.
Unlike phones, a laptop or PC can execute arbitrary code. In this example above, the file extension appears to end in a .pdf, but like email addresses, file extensions can be spoofed or masked. And some file formats, including .docx, .psd, and others, can be used as vectors for malware, ransomware, and viruses. They’re not fool-proof, but generally iOS and Android devices have a security architecture that makes them a little more resilient to threats than PCs and Macs.
Want more? Check out the rest of this email security series.
Does your team need some cybersecurity help?
VPC can conduct onsite, interactive, tabletop, and virtual cybersecurity training and audits that go beyond email security.
We’ve worked with the Midwest’s largest governments, enterprises, and healthcare providers to audit, protect, and train organizations to react and respond to malware, ransomware, cybersecurity, and more.


















