This post is part of a series. Practical email security guide » Spear phishing can originate from your website and social media

Spear phishing is a one-to-few or one-to-one kind of attack. Companies and groups with a public directory or staff listing on their websites have probably encountered one of these in the past.
A common spear phishing attack works and looks like this:
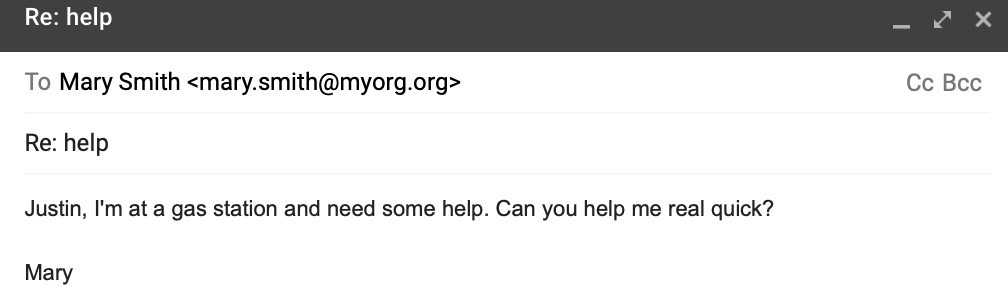
Let’s assume the email address mary.smith@myorg.org looks valid to you and you recognize Mary Smith and her name as someone close to you. Let’s also assume it’s written to you, your name, and sounds perfectly reasonable.
When presented with an email from your boss or organization president, most people will likely act on it quickly. In your haste, you reply, “Sure. What do you need?”
Now the person on the other end of this process, who is not really Mary, knows you exist. They will usually reply with some request to purchase several gift cards, send cash, or other valuable asset that’s hard to trace.
The stories are often convincing. The next reply from your “boss” will likely read like this:
I’m at the gas station trying to buy some gift cards for the team and they’re out of Visa gift cards. Can you purchase a handful online and send me the activation codes?
For a lot of people, that seems like a semi-reasonable request. The only thing that might set off suspicion is style. “Mary usually refers to us as the staff, not the team,” for instance.
What makes spear phishing so nefarious is how real it is and how vague the requests are. There’s so little information to work from, even just “a handful” of gift cards. Does she need three or thirty?
We’ve seen this kind of email attack before and to add to the realism, they often come after work hours or on weekends—times when you don’t know where your supervisor really is.
How does spear phishing work? How do they even know this about me and my team?
- A malicious user—or a thief, really—can look at your website’s staff listing.
- They can identify the email address and name of the person in charge.
- They can also identify the names and email addresses of the people working under them, or even cross-check information on LinkedIn.
- By using “domain spoofing”, a user can pretend to email from your boss’ address. This is no more difficult than changing the “from” details in Outlook, Apple Mail, or any email application.
- So long as they use language that’s casual, vague, and not riddled with typos, this spear phishing attack can be highly effective.
Protect yourself and your team from spear phishing attacks
- Ensure everyone on the team is using a consistent email signature on all devices. Often signatures are setup on a laptop, but not a phone. Even if it’s just listing their name, title, and phone number, you’ll get used to seeing this consistently. It’s unlikely an attacker would know precisely how to format and include those details. Set consistency in things like phone numbers, so you always know your team writes phone numbers as 555-555-5555 and not 555.555.5555.
- Hit “reply” on the email, but look closely at where the reply-to address points. This is where domain spoofing stops and reveals the actual address. If it’s fake or unknown, delete it and move on.
- If a word or stylisting choice strikes you as odd, don’t reply to the email. There’s no harm in the initial reply. The harm is obviously handing over cash or money. Instead, call or text the suspected person you’re emailing to ask if they’re really asking for gift cards.
- Consider hiding emails on your website and list only names and titles of staffers. Emails can go through Contact Us forms instead.
Want more? Check out the rest of this email security series.
Does your team need some cybersecurity help?
VPC can conduct onsite, interactive, tabletop, and virtual cybersecurity training and audits that go beyond email security.
We’ve worked with the Midwest’s largest governments, enterprises, and healthcare providers to audit, protect, and train organizations to react and respond to malware, ransomware, cybersecurity, and more.


















