This post is part of a series. Practical email security guide » The danger of phishing emails

“Phishing” means any kind of email that’s sent from one person or bot to many people in hopes someone will click a link that leads to a malicious website or exploits some bug.
Phishing emails are typically sent from bots or overseas actors who acquire email addresses from places that have been severely compromised, like major retailers. U.S. cellular companies are frequent victims of these robust, orchestrated hacks because virtually every adult in the U.S. has their email on file with one of the three major cellular carriers. As opposed to, say, a small regional grocery chain.
In this circumstance, your email address is leaked and now you’re getting emails. Some are obviously spam and get sorted into the spam folder. Others sometimes slip through.
Can you tell the difference between these emails?
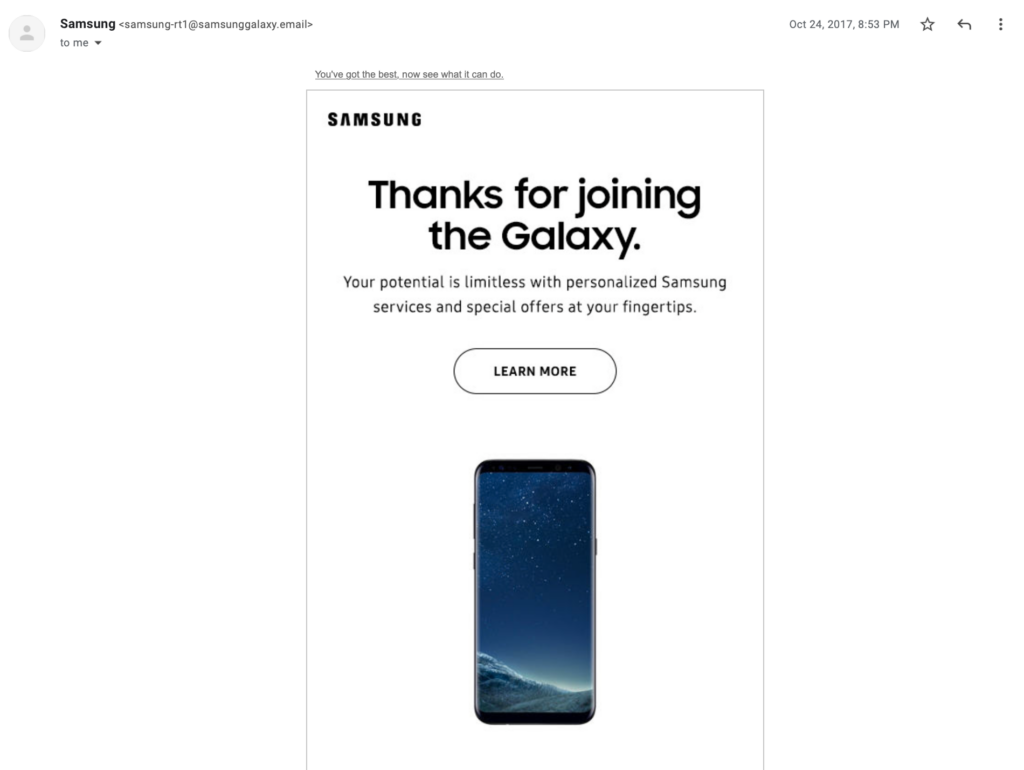

You can’t tell because there is no difference. At least no visible difference. The “Learn more” button is what’s different, one with a link to a real webpage from the manufacturer and another that’s malicious. Assuming you actually owned this model of phone, it might be hard to discern what to do with it.
It’s designed to direct you to a website that, the attacker hopes, will fool you into inputting the email or password to your carrier, or maybe a credit card number, or potentially your birthday or setup a secret question for password recovery.
To avoid this attack, you’d need to be aware of where it leads you and recognize the signs of a secure webpage in your browser and check the URLs it directs you to. This includes a correctly spelled URL, a lock icon to indicate it’s a secure webpage using “https” instead of “http”, and that the webpage ‘feels right’ by using correct spellings, language, and style.
Want more? Check out the rest of this email security series.
Does your team need some cybersecurity help?
VPC can conduct onsite, interactive, tabletop, and virtual cybersecurity training and audits that go beyond email security.
We’ve worked with the Midwest’s largest governments, enterprises, and healthcare providers to audit, protect, and train organizations to react and respond to malware, ransomware, cybersecurity, and more.


















