Data breaches to date
As required by HITECH and HIPAA, covered entities must report healthcare data breaches of unsecured protected health information (PHI) affecting 500 or more individuals to HHS’s Office for Civil Rights (OCR).
For 2021, The OCR’s Breach Portal’s entries show the continuation of a troubling trend—as the pandemic continues to overwhelm providers and threat actors get savvier, healthcare data breaches are not slowing down. OCR named over 550 covered entities that have experienced a data breach in 2021, at the time of publication. Over 40 million individuals faced PHI exposure as a result of these breaches.
The 10 biggest reported healthcare data breaches of 2021 (by the number of individuals affected) were all hacking/IT incidents, and all but one occurred on the organization’s network server. Ransomware continues to be a threat across the healthcare sector, and the trend is likely to continue in 2022. The examples are as follows:
- Health plan Florida Healthy Kids Corporation started the year by reporting the biggest healthcare data breach of 2021 to date on January 29. The breach impacted 3.5 million individuals. (3,500,000)
- Florida-based 20/20 Eye Care Network reported a healthcare data breach to HHS on May 24. According to a notice from the Maine attorney general’s office, 20/20 discovered suspicious activity on its Amazon Web Services (AWS) environment on January 11, 2021. Over 3.2 million individuals were notified that their Social Security numbers, names, addresses, member identification numbers, birth dates, and health insurance information may have been exposed or deleted. (3,253,822)
- Forefront Dermatology, S.C., notified HHS on July 8 of a data breach that impacted over 2.4 million individuals, including patients and employees. The dermatology practice identified a network intrusion on June 4 and promptly took its network offline. (2,413,553)
- NEC Networks, which does business under the name CaptureRx, faced a healthcare data breach in February that impacted over 1.6 million people and impacted more than 16 healthcare organizations. CaptureRx is an IT vendor that helps healthcare systems manage their 340B drug programs. (1,656,569)
- Indianapolis-based Eskenazi Health notified HHS of a data breach on October 1. The breach was discovered on August 4 and led to significant EHR downtime and ambulance diversions. (1,515,918)
- The Kroger Co. reported a healthcare data breach to HHS on February 19. The grocery chain was one of over 100 victims of the Accellion data breach, which occurred in December 2020 and impacted a dozen healthcare organizations. (1,474,284)
- St. Joseph’s/Candler (SJ/C) Health System in Savannah, Georgia discovered a ransomware attack on June 17 that led to significant EHR downtime. Further investigation determined that the breach began on December 18, 2020. The hospital system’s computers and telecommunications systems were inaccessible, and clinicians had to document clinical notes on pen and paper. (1,400,000)
- University Medical Center Southern Nevada fell victim to a REvil/Sodinokibi ransomware attack in June that compromised files containing the personal information of 1.3 million individuals. The hackers also posted photos of passports, Social Security cards, and driver’s licenses on the dark web for about a dozen individuals. (1,300,000)
- New York-based American Anesthesiology (owned by North American Partners in Anesthesia) client information was exposed when an unauthorized party gained access to the email system of the practice’s business associate, MEDNAX. (1,269,074)
- In July, practice management vendor Professional Business Systems, doing business as Practicefirst, announced that a 2020 ransomware attack had potentially exposed the PHI of patients and employees. (1,210,688)
The new paradigm for 2021 and beyond
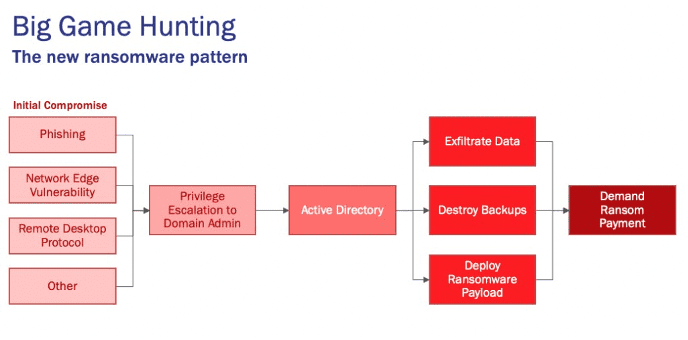
- Like ransomware attacks, data breaches are a major plague to healthcare in cyberspace.
- Through double extortion, these two attacks are often combined.
- Ransomware attacks were responsible for almost 50% of all healthcare data breaches in 2020.
- Healthcare is the most targeted sector for data breaches.
- VPNs protect organizations from many forms of attacks, but VPN vulnerabilities can leave users and organizations at risk:
- 34% of IT security teams across the globe claim to be in the process of implementing a Zero Trust security model (Gartner).
- “ZeroTrust is a security concept that requires all users, even those inside the organization’s enterprise network, to be authenticated, authorized, and continuously validating security configuration and posture, before being granted or keeping access to applications and data.” – CrowdStrike
- Gartner predicts 60% of enterprises will be phased out of VPNs in favor of Zero Trust network access by 2023.
- The SolarWinds breach was not an isolated incident
- Organizations are put at risk not just by their own attack surface, but by the attack surface of their vendors
- Continued threats from 2020/2021:
- Targeting of home environments and vulnerabilities introduced through COVID-19 protocolsl ike WFH.
- Pre-pandemic, 82% of organizations used some form of Bring Your Own Device (BYOD) for employees, partners, or other stakeholders.
- 72% lacked BYOD malware protection entirely, or relied upon endpoint software installations.
- Pandemic forced more organizations to allow BYOD.
- Security management solutions are available for organizations that allow BYOD.
- WFH exposed corporate resources to home networks.
- COVID-19 phishing campaigns
- Vaccine rollout
- Targeting of COVID-19 research and vaccine distribution:
- From FireEye: 2020 featured “targeting of hospitals, manufacturing groups and related critical infrastructures dedicated to development and distribution of a COVID-19 vaccine.”
- “Increasing numbers of state-sponsored actors targeting coronavirus research, treatment and response efforts. This direct targeting of government, healthcare, pharmaceutical and non- governmental organizations will likely continue due to the high-value information involved.”
- Cybersecurity firm WatchGuard predicts that “cybercriminals have already started to create tools that can automate the manual aspects of spear phishing.”
- This automation could combine the automation of phishing with the highly targeted nature of spear phishing.
- Ongoing instability and uncertainty from the global pandemic makes all phishing attempts more effective.
Financial impact and projections
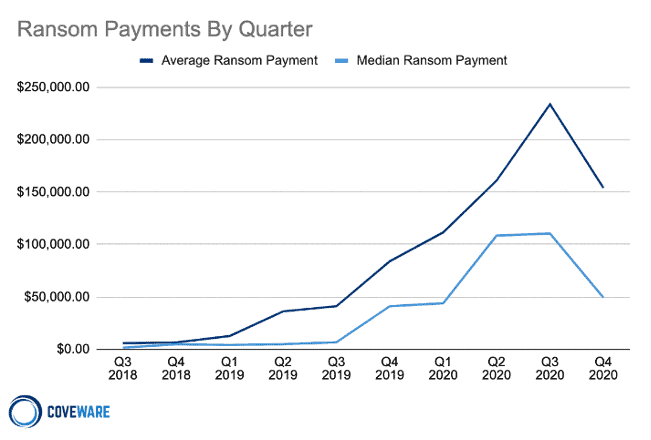
Health care data breach costs are consistently the highest of any industry. In 2021, the Cost of a Data Breach report found the cost of a health care data breach reached $9.23 million (a 29% increase over 2020).
Cybersecurity Ventures predicts that the healthcare industry will spend upwards of $125 billion cumulatively on cybersecurity products and services from 2020-2025.
Hospitals spend 64 percent more annually on advertising after a breach over the following two years, according to a Dec. 2018 report from the American Journal of Managed Care.
Four to seven percent of a health system’s IT budget is in cybersecurity, compared to about 15 percent for other sectors such as the financial industry, according to a former federal prosecutor who is now focused on advising healthcare providers and medical device companies on matters related to civil and criminal healthcare fraud and abuse, as well as government investigations and enforcement.
IT research firm Gartner predicts that in 2020, more than 25 percent of cyberattacks in healthcare delivery organizations will involve the Internet of Medical Things (IoMT). To be clear, in medical terms, that means wirelessly connected and digitally monitored implantable medical devices (IMDs) — such as cardioverter defibrillators (ICD), pacemakers, deep brain neurostimulators, insulin pumps, ear tubes, and more.
Who poses the biggest security threats to healthcare information systems?
- Foreign Intelligence Agencies have offensive security capabilities and may also seek to compromise healthcare information systems to exfiltrate research data, such as NCSC issued APT29 cybercrime group targeting COVID-19 vaccine development efforts globally.
- Insider threats come from employees who may be negligent, unintentional or problematic insiders.
- Phishing attacks utilising phishing and spam emails (unsolicited email with false and hidden information) aimed at stealing sensitive patient information and for monetary gains
- Cybercrime groups carrying out targeted campaigns using social engineering attack techniques to commit identity frauds
- Bot-network operators that control vulnerable system access and trade it illegally on the darkweb for monetary gains that in turn are used for Denial of Service (DoS) attacks, phishing or relaying spam emails.
- Espionage at the industrial, staff or nation-state level to gain a competitive edge.
Recommendations
Create a culture of cybersecurity. While technology is clearly critical in the fight to detect and stop intrusions, the end user remains a crucial link in the chain to stop breaches. User awareness programs should be initiated to combat the continued threat of phishing and related social engineering techniques.
Make sure you have a current cybersecurity policy that accounts for remote working. Security policies need to include access management for remote workers, the use of personal devices, and updated data privacy considerations for employee access to documents and other information.
Protect identities and access. Organizations must consider multifactor authentication (MFA) on all public-facing employee services and portals as mandatory. In addition to MFA, a robust privilege access management process will limit the damage adversaries can do if they get in, and reduce the likelihood of lateral movement. Finally, Zero Trust solutions should be implemented to compartmentalize and restrict data access, thus reducing the potential damages from unauthorized access to sensitive information.
If you can’t see it, you can’t protect it. For security teams operating in today’s environment, visibility and speed are critical for blocking attackers that have the capability and intent to steal data and disrupt operations. Security teams must understand that it is their responsibility to secure their cloud environments, just as they would on-premises systems. They must establish consistent visibility for all environments and proactively address potential vulnerabilities before they can be leveraged by attackers.
Invest in expert threat hunting. Interactive attacks use stealthy or novel techniques designed to bypass automated monitoring and detection. Continuous threat hunting is the best way to detect and prevent sophisticated or persistent attacks.
Get ahead of attackers with threat intelligence. There is a human being behind every attack. Threat intelligence helps you understand an attacker’s motivation, skills, and tradecraft so you can use this knowledge to your advantage to prevent, and even predict future attacks.
Phishing
- Train employees to recognize phishing emails
Ransomware
- Maintain an incident response plan
- Maintain backups of data (3-2-1 rule)
- Patch vulnerabilities
Supply Chain Attacks
- Ask vendors what mechanism they have in place to protect their software from compromise • Apply policy of least-privilege to applications and software
VPN Vulnerabilities
- Consider shifting to Zero Trust security framework
Internet of Medical Things (IoMT)
- Knowing is half the battle: identify all devices and vulnerabilities
- Initiate micro-segmentation
- Establish manageable and realistic network security parameters
- Maintain existing network assets and infrastructure
The data gathered and presented in this report comes from a number of sources, specifically, they are:
- Health and Human Services Cybersecurity Program
- Crowdstrike
- The Ponemon Institute
- Health IT Security
- Parachute
- Herjavec Group
- Nord
- Security Intelligence
- Coveware
- Cybersecurity Ventures
Data presented is current as of Nov. 30, 2021

















